RANSOMWARE: WHAT IT IS AND HOW TO COMBAT IT
By Sangee S.
WHAT IS IT?
Ransomware is essentially a form of malware that attacks a user’s computer, except more dangerous. Ransomware blocks access to an individual’s system by encrypting all the files on their computer. In most cases, in order for the user to regain access to their system, they are forced to pay a ransom or risk losing their files forever.
Since ransomware is a type of malware, it can be triggered using the same mechanisms as other types of malware. For example, an individual may receive a spam email with an archived attachment which prompts the user to download. After downloading the attachment the malware then connects to specific URLs where the crypto-ransomware is hosted and automatically downloads onto the user’s computer, encrypting all of the files on the now affected computer system. A ransom message is then displayed to the user, stating the amount the individual must pay as well as the deadline for payment. A visual of this process can be seen below:
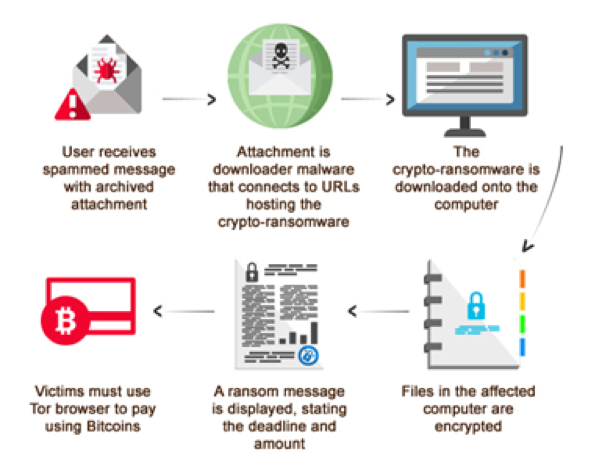
Image Credit: Trend Micro
It is important to note in this diagram that most cases of Ransomware require the user to pay in Bitcoins in order to regain access to their files. The reason for this is so that authorities cannot track who and where the money is going to. Born in 2009, Bitcoin is a digital currency that is essentially anonymous, which means authorities will have difficulties tracking transactions made through it.
Some of the key characteristics that set ransomware apart from other types of malware include:
- Unbreakable encryption which prohibits users from decrypting the files on their own;
- Ability to encrypt all kinds of files regardless of the file type. This means all types of media and documents are susceptible to encryption;
- Displays a message or an image onto the user’s screen that notifies them of their encrypted data while prompting for payment;
- Payment is made in Bitcoins rather than traditional currencies;
- There is a time-limit in which the user is required to pay the ransom. Going over the time-limit could either mean an increase in ransom fees or loss of data altogether;
- Use of a complex set of evasion techniques which protect it from being detected by traditional antivirus software;
- It can recruit the user’s infected PC into botnets (entire networks of computers that are instructed to do things such as attack other computers or deliver spam/spyware/ransomware), which allows cyber criminals to expand their infrastructure and fuel future attacks;
- It can spread to other PCs that are connected to a local network
- It can extract data such as usernames, passwords, and email addresses which can be sent to a server controlled by cyber criminals.
- It is important to note that not only can ransomware encrypt data, but it is also capable of much more.
Types of Ransomware:
• ZCrptor
• TeslaCrypt
• KeRanger
• Jigsaw
• CryptoLocker
• CryptoWall
• Torrent Locker
• WannaCry
COMBATING RANSOMWARE CYBER THREATS:
Simply being aware and knowing what ransomware is can go a long way in securing the data and information of a user’s system.
Since ransomware is a type of malware, traditional approaches to combating malware can be applied in this case. For example, it is imperative for users to thoroughly inspect emails before opening them. Users must be wary of emails from unverified sources. It also important for users to avoid clicking embedded links and downloading attachments found in unverified emails. This could lead to the download of ransomware onto the individual’s system.
Backing up important files is a key contributor in lessening the potential damage done by a ransomware attack. By having a backup, users can retrieve important files while being locked out of their system.
Regularly updating software, programs, and applications to their latest versions can also provide added protection against ransomware attacks. Having the latest version of software and applications means that all patches are up-to-date and the risk of vulnerability is lower.
Piqued your curiosity?
Register now for the Toronto Chapter Event
Ransomware/Bitcoin/Blockchain Technologies
with speakers
Iliana Oris Valiente, Certified Bitcoin Professional
and Moustafa Naguib, of Superior Propane
About the Author:
Sangee Selvanathan has completed his commerce degree, majoring in Business Technology Management at Ted Rogers School of Management, Ryerson University. He enjoys all things technology-related as well as using technology to drive business solutions in the workplace.